How to Stay Safe in the New World of Hybrid Work
Have you ever wondered what it would be like to work from anywhere, anytime, and on any device? Well, you’re not alone. Many people and organizations are embracing hybrid work, a new way of working that combines remote and in-office work. Hybrid work can give you more flexibility, autonomy, and work-life balance. It can also help your organization save costs, attract talent, and increase productivity. Sounds awesome, right?
But wait, there’s a catch. Hybrid work also comes with some security challenges. You see, when you work from different places and devices, you also expose yourself and your organization to more cyber threats. Hackers are always looking for ways to compromise your accounts, devices, or networks. They can use phishing emails, ransomware attacks, firmware hacks, and other nasty tricks to steal your data or money.
So how can you protect yourself and your organization from these cyber threats? How can you enjoy the benefits of hybrid work without sacrificing security? The answer is simple: Zero Trust.
What is Zero Trust?
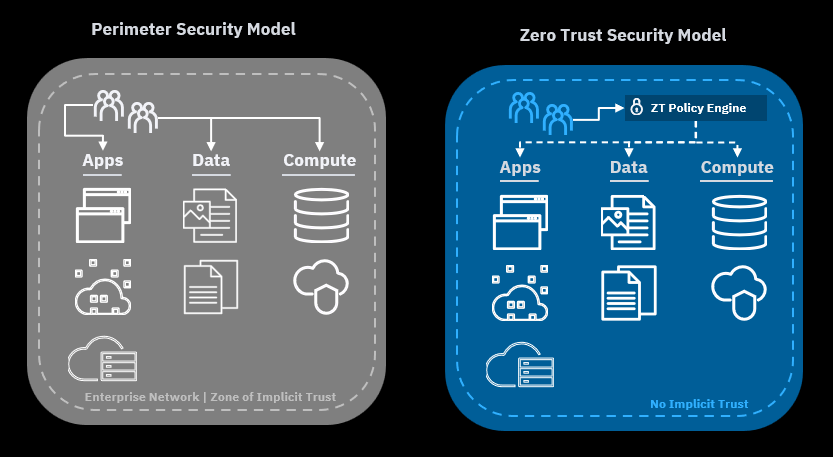
Zero Trust is a security mindset that says you should never trust anyone or anything online. It doesn’t matter if you’re on your home network or your office network. It doesn’t matter if you’re using your personal laptop or your work tablet. It doesn’t matter if you’re logging into your email or your cloud service. You should always verify who you are and what you’re doing before you access anything online.
Zero Trust is based on three principles: verify explicitly, grant least privileged access, and assume breach.
- Verify explicitly: This means you should always prove your identity before you access anything online. The best way to do this is by using multi-factor authentication (MFA), which requires two or more factors of authentication, such as a password and a code sent to your phone. MFA can stop hackers from logging into your accounts even if they have your password.
- Grant least privileged access: This means you should only access what you need and nothing more. The best way to do this is by using conditional access, which evaluates the context and risk of every access request and enforces granular controls based on various factors such as user identity, device health, location, app sensitivity, etc. Conditional access can allow, block, or limit access based on the level of trust and need.
- Assume breach: This means you should always act as if you or your organization have been compromised. The best way to do this is by using encryption and VPNs, which protect your data from unauthorized access or modification. Encryption transforms your data into an unreadable form using a secret key. VPNs create a secure tunnel between your device and your organization’s network over the internet. Encryption and VPNs can keep your data safe even if hackers intercept or tamper with it.
How to Make Zero Trust Work for You
You might be thinking that Zero Trust sounds great, but how do you actually do it? Well, it’s not as hard as you might think. You just need to follow some simple steps to make Zero Trust work for you and your organization. Here they are:
- Think about what you want to achieve with Zero Trust: The first step is to think about what you want to achieve with Zero Trust. What are the benefits and values of Zero Trust for you and your organization? How will it help you improve your security and business outcomes? How will you know if you’re doing it right? You can use some online tools like Microsoft’s Zero Trust Assessment tool or NIST’s Zero Trust Architecture publication to help you think about what you want to achieve with Zero Trust.
- See where you are today and what you need to improve: The second step is to see where you are today and what you need to improve. How secure are you and your organization today? What are the good and bad things about your current security model? What are the things that need to be fixed or changed? Take a look at Microsoft’s Zero Trust Maturity Model to help you see where you are today and what you need to improve.
- Make a plan and decide what to do first: The third step is to make a plan and decide what to do first. How will you go from where you are today to where you want to be with Zero Trust? What are the main things that you need to do? How do they relate to each other? How long will they take? You can use this useful roadmap as a reference to help you make a plan.
- Do it and check how it’s going: The fourth step is to implement your plan and track your results. You’ll need to assign roles and responsibilities to the people who will help you with the execution, allocate the necessary resources, set realistic deadlines, and define the metrics and indicators that will show you how well you are doing and what problems you need to solve. To help yourself implement changes and track results you can use online tools like Azure Active Directory or hire cybersecurity professionals to do that for you.
- Learn from your experience and keep improving: The fifth step is to evaluate your performance and enhance your approach. You’ll need to analyze the data and feedback that you collected, identify the strengths and weaknesses of your Zero Trust adoption, recognize the new threats or opportunities that you face, and update or modify your plan based on your evaluation.
How to Overcome the Challenges and Barriers of Adopting Zero Trust
You might think that adopting Zero Trust is too hard or too expensive or too disruptive for your organization. You might have heard some myths or misconceptions that make you hesitate or resist the change. Well, don’t let these challenges and barriers stop you from achieving better security and business outcomes. Here are some tips and best practices on how to overcome them:
- Get leadership buy-in: One of the most important factors for a successful Zero Trust adoption is having the support and commitment of your senior leaders. They can help you set the vision and goals, allocate the resources and budget, and drive the culture change. You can convince them by showing them the benefits and value of Zero Trust, such as improved security posture, reduced risk, increased productivity, and enhanced customer trust.
- Build a cross-functional team: Another key factor for a successful Zero Trust adoption is having a cross-functional team that can collaborate and coordinate across different domains and disciplines. You need people from security, IT, business, legal, compliance, and other functions to work together and align on the strategy, design, implementation, and operation of Zero Trust. You can use frameworks like Microsoft’s Zero Trust Maturity Model or leverage existing communities and networks, such as Microsoft’s Zero Trust Community or SANS’s Cybersecurity Community, to learn from others and share best practices.
- Communicate clearly and frequently: A third key factor for a successful Zero Trust adoption is having clear and frequent communication with your stakeholders and users. Explain to them what Zero Trust is and why it matters, what changes are expected and how they will benefit, and what support and resources are available. Use simple and consistent language that avoids jargon and technical details, and try to solicit feedback and input from your stakeholders and users to address their concerns and questions.
- Leverage existing resources and partners: A fourth key factor for a successful Zero Trust adoption is leveraging existing resources and partners that can help you accelerate your journey. You don’t have to start from scratch or reinvent the wheel. You can use existing tools and solutions that are designed for Zero Trust, such as Microsoft 365 or Azure Active Directory. You can also partner with experts that can provide guidance and support.
Hopefully, these tips and best practices will help you overcome the challenges and barriers of adopting Zero Trust for your hybrid work environment.
The Bottom Line: Zero Trust is the Way to Go for Hybrid Work
Hybrid work is a new reality that offers many benefits but also poses many security challenges. To stay safe in the new world of hybrid work, you need to adopt a Zero Trust mindset and follow its principles: verify explicitly, grant least privileged access, and assume breach. By doing so, you can protect yourself and your organization from cyber threats and enjoy the benefits of hybrid work without sacrificing security. Remember, security is not only a tech problem but also a human problem. It’s up to you to make a difference and be part of the solution.
Don’t let cyber threats ruin your hybrid work experience. Start your Zero Trust journey today and enjoy the benefits of flexibility, autonomy, and work-life balance without sacrificing security.